Introduction
This article will cover how to inject secrets in Pods using Hashicorp Vault. In previous articles, we covered how to install Hashicorp Vault in Kubernetes, configure and create secrets in Hashicorp, and how tools such as TIBCO BW can retrieve them. Still, today, we are going to go one step ahead.
The reason why Inject secrets in pods is very important is that it allows the application inside the pod to be transparent around any communication to Hashicorp. After all, for the applications, the secret will be just a regular file located in a specific path inside the container. It doesn’t need to worry if this file came from a Hashicorp Secret or a total of different resources.
This injection approach facilitates the Kubernetes ecosystem’s polyglot approach because it frees any responsibility for the underlying application. The same happens with injector approaches such as Istio or much more.
But, let’s explain how this approach works to inject secrets in Pods using Hashicorp Vault. As part of the installation alongside the vault server we have installed (or several ones if you have done a distributed installation), we have seen another pod under the name of value-agent-injector, as you can see in the picture below:

This agent will be responsible for listening to the new deployments you do and, based on the annotations this deployment has, will launch a sidecar alongside your application and send the configuration to be able to connect to the vault and download the secrets required and mount it as files inside your pod as shown in the picture below:
To do that, we need to do several steps as part of the configuration as we are going to include in the upcoming sections of the article
Enabling Kubernetes Authentication in Hashicorp
The first thing we need to do at this stage is to enable the Kubernetes Authentication in Hashicorp. This method allows clients to authenticate with a Kubernetes Service Account Token. We do that with the following command:
Vault auth enable kubernetesVault accepts a service token from any client in the Kubernetes cluster. During authentication, Vault verifies that the service account token is valid by querying a token review Kubernetes endpoint. Now, we need to configure this authentication method providing the location our the Kubernetes API, and to do that, we need to run the following command:
vault write auth/kubernetes/config \
kubernetes_host="https://$KUBERNETES_PORT_443_TCP_ADDR:443"Defining a Kubernetes Services Account and Defining a Policy
Now, we will create a Kubernetes Service Account that will run our pods, and this service account will be allowed to retrieve the secret we generated in the previous post.
To do that, we will start with the creation of the service account by running this command from outside the pod:
kubectl create sa internal-appThis will create a new service account under the name of internal-app, and now we are going to generate a policy inside the Hashicorp Vault server by using this command inside the vault server pod:
vault policy write internal-app - <<EOF
path "internal/data/database/config" {
capabilities = ["read"]
}
EOFAnd now, we associated this policy with the service account by running this command also inside the vault server pod:
vault write auth/kubernetes/role/internal-app \
bound_service_account_names=internal-app \
bound_service_account_namespaces=default \
policies=internal-app \
ttl=24hAnd that’s pretty much all the configuration we need to do at the Vault side to be able to inject secrets in pods using Hashicorp Vault. Now, we need to configure our application accordingly by doing the following modifications:
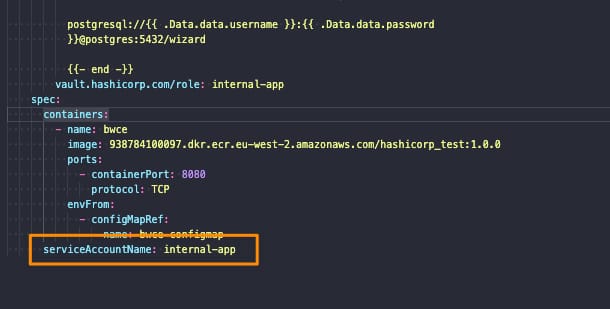
- Specify the ServiceAccountName to the deployment to be the one we created previously: internal-app
- Specify the specific annotations to inject the vault secrets and the configuration of those secrets.
Let’s start with the first point. We need to add the serviceAccountName to our Kubernetes Manifest YAML file as shown below:
And regarding the second point, we would solve it by adding several annotations to our deployment, as shown below:
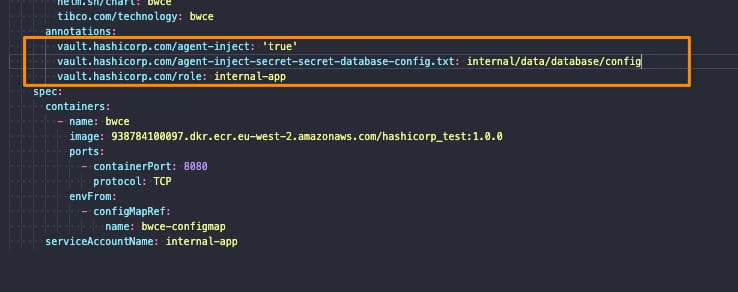
The annotations used to inject secrets in pods are the following ones:
- vault.hashicorp.com/agent-inject: ‘true’: This tells the vault injector that we would like to inject the sidecar agent in this deployment and have the Vault configuration. This is required to do any further configuration
- vault.hashicorp.com/role: internal-app: This is the vault role we are going to use when we’re asking for secrets and information to the vault to be sure that we only access the secrets we have allowed based on the policy we created in the previous section
- vault.hashicorp.com/agent-inject-secret-secret-database-config.txt: internal/data/database/config: This will be one annotation per secret we plan to add, and it is composed of three parts:
- vault.hashicorp.com/agent-inject-secret- this part is fixed
- secret-database-config.txt this part will be the filename that is created under /vault/secrets inside our pod
- internal/data/database/config This is the path inside the vault of our secret to being linked to that file.
And that’s it! If we deploy now our deployment we will see the following things:
- Our deployment application has been launched with three containers instead of one because two of them are Hashicorp Vault related, as you can see in the picture below:
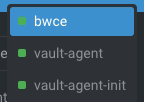
- vault-agent-init will be the container that establishes the connection to the vault-server because any container starts and does the first download and injecting secrets in the pod based on the configuration provided.
- vault-agent will be the container running as a watcher to detect any modification on the related secrets and update them.
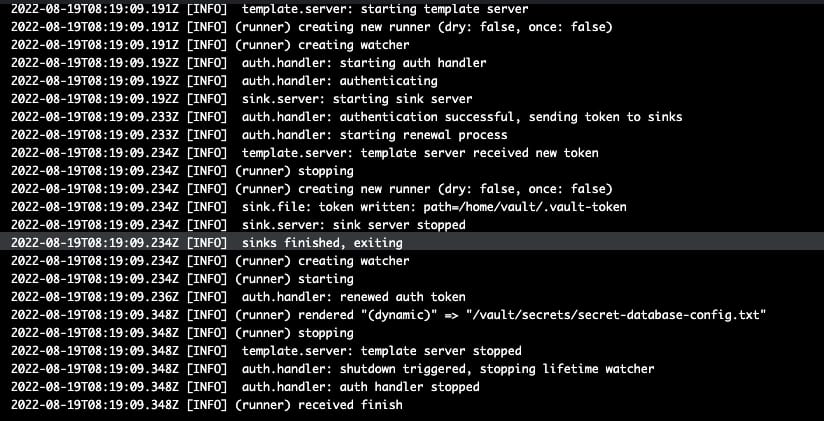
And now, if we go to the main container, we will see in the /vault/secrets path the secret has been finally injected as expected:
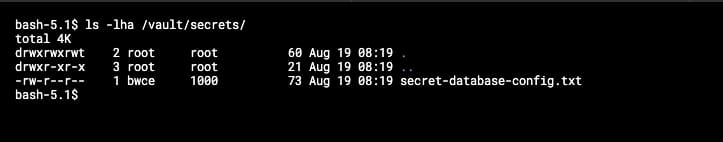
And this is how easily and without any knowledge about the underlying app we can inject secrets in pods using Hashicorp Vault.
📚 Want to dive deeper into Kubernetes? This article is part of our comprehensive Kubernetes Architecture Patterns guide, where you’ll find all fundamental and advanced concepts explained step by step.