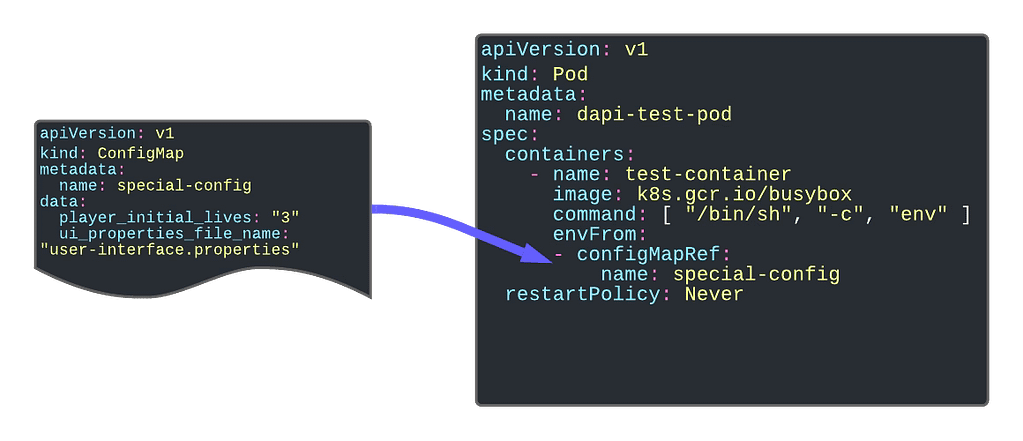
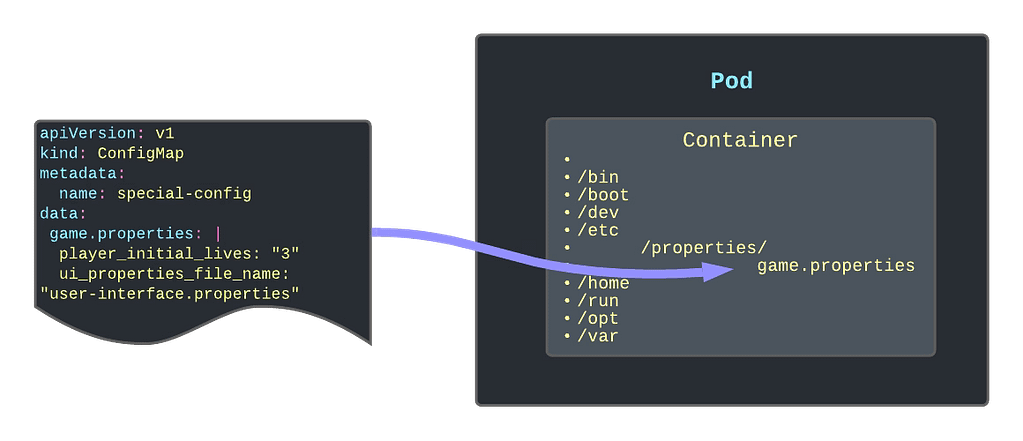
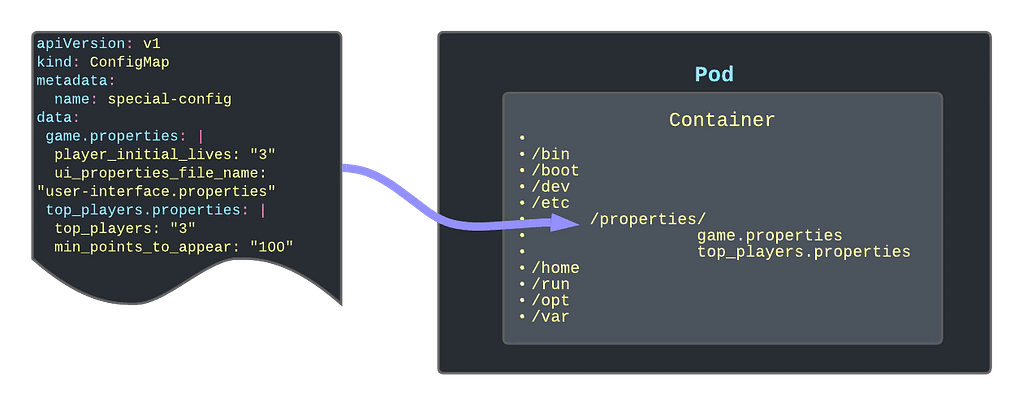
Kubernetes ConfigMaps are a powerful tool for managing configuration data separately from application code. However, they can sometimes lead to issues during deployment, particularly when a ConfigMap referenced in a Pod specification is missing, causing the application to fail to start. This is a common scenario that can lead to a CreateContainerConfigError and halt your deployment pipeline.
Understanding the Problem
When a ConfigMap is referenced in a Pod’s specification, Kubernetes expects the ConfigMap to be present. If it is not, Kubernetes will not start the Pod, leading to a failed deployment. This can be problematic in situations where certain configuration data is optional or environment-specific, such as proxy settings that are only necessary in certain environments.
Making ConfigMap Values Optional
Kubernetes provides a way to define ConfigMap items as optional, allowing your application to start even if the ConfigMap is not present. This can be particularly useful for environment variables that only need to be set under certain conditions.
Here’s a basic example of how to make a ConfigMap optional:
apiVersion: v1
kind: Pod
metadata:
name: example-pod
spec:
containers:
- name: example-container
image: nginx
env:
- name: OPTIONAL_ENV_VAR
valueFrom:
configMapKeyRef:
name: example-configmap
key: optional-key
optional: true
In this example:
name: example-configmaprefers to the ConfigMap that might or might not be present.optional: trueensures that the Pod will still start even ifexample-configmapor theoptional-keywithin it is missing.
Practical Use Case: Proxy Configuration
A common use case for optional ConfigMap values is setting environment variables for proxy configuration. In many enterprise environments, proxy settings are only required in certain deployment environments (e.g., staging, production) but not in others (e.g., local development).
apiVersion: v1
kind: ConfigMap
metadata:
name: proxy-config
data:
HTTP_PROXY: "http://proxy.example.com"
HTTPS_PROXY: "https://proxy.example.com"
In your Pod specification, you could reference these proxy settings as optional:
apiVersion: v1
kind: Pod
metadata:
name: app-pod
spec:
containers:
- name: app-container
image: my-app-image
env:
- name: HTTP_PROXY
valueFrom:
configMapKeyRef:
name: proxy-config
key: HTTP_PROXY
optional: true
- name: HTTPS_PROXY
valueFrom:
configMapKeyRef:
name: proxy-config
key: HTTPS_PROXY
optional: true
In this setup, if the proxy-config ConfigMap is missing, the application will still start, simply without the proxy settings.
Sample Application
Let’s walk through a simple example to demonstrate this concept. We will create a deployment for an application that uses optional configuration values.
- Create the ConfigMap (Optional):
apiVersion: v1
kind: ConfigMap
metadata:
name: app-config
data:
GREETING: "Hello, World!"
- Deploy the Application:
apiVersion: apps/v1
kind: Deployment
metadata:
name: hello-world-deployment
spec:
replicas: 1
selector:
matchLabels:
app: hello-world
template:
metadata:
labels:
app: hello-world
spec:
containers:
- name: hello-world
image: busybox
command: ["sh", "-c", "echo $GREETING"]
env:
- name: GREETING
valueFrom:
configMapKeyRef:
name: app-config
key: GREETING
optional: true
- Deploy and Test:
- Deploy the application using
kubectl apply -f <your-deployment-file>.yaml. - If the
app-configConfigMap is present, the Pod will output “Hello, World!”. - If the ConfigMap is missing, the Pod will start, but no greeting will be echoed.
Conclusion
Optional ConfigMap values are a simple yet effective way to make your Kubernetes deployments more resilient and adaptable to different environments. By marking ConfigMap keys as optional, you can prevent deployment failures and allow your applications to handle missing configuration gracefully.
📚 Want to dive deeper into Kubernetes? This article is part of our comprehensive Kubernetes Architecture Patterns guide, where you’ll find all fundamental and advanced concepts explained step by step.